What do you know about special MERNUS science lab emergency shower in some labs to protect you in case of an emergency? It’s known as a lab emergency shower, and it’s a crucial piece of safety equipment that every lab should have. In this excerpts, we will cover what a lab emergency shower does, how to use it correctly, why your lab needs one, and what it does.
A lab emergency shower (somewhat contrarily) is a safety mechanism to use if a dangerous chemical falls on somebody’s skin. The quick rinse-off of harmful substances is intended to reduce injury.
Yes, you see the MERNUS lab science emergency shower near or under the sink and think, Good to know where it is! The shower is joined by a lever or button that you must pull to turn on it. After the water is on, step into it and allow water to wash away the harmful substance for a minimum of 15 minutes. Also remove any clothes that may have come in contact with the toxic material so you don’t spread the damage further.

So the periodic checking of MERNUS science lab emergency shower to keep it functional, is equally important. Test the shower at least once a month to make sure the water flows and is the right temperature. If you notice any issues with the shower, inform the lab supervisor so that it can be repaired or replaced in a timely manner.

They have access to a lab self contained emergency shower Very business Safety. In the event of a chemical spill or injury, rapid access to a decontamination shower can prevent serious injury and minimize health risk. Having lab emergency shower means creating a safe and secure work environment.
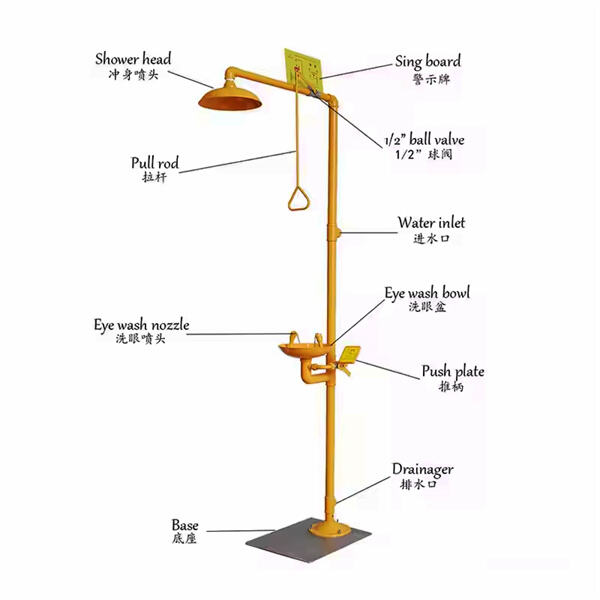
It is important to have an self contained emergency shower station in the lab. Quick access to a shower can potentially save a life in the event of an accident. By having an emergency shower, you are not just safe yourself and spare your coworkers, but you can also prevent environmental pollution.
Our proficiency in project management is the result of a meticulous approach to orchestrating complex security initiatives. We bring to bear a synergy of strategic vision and operational agility, ensuring that each project is executed with the precision of a Swiss watch. Our project managers are seasoned navigators of the security implementation process, guiding our clients through the intricacies of their security projects with a deft hand, providing them with the confidence that their security posture is in capable and experienced hands.
We understand that the security needs of our clients are as diverse as the businesses they represent. This understanding has led us to specialize in crafting bespoke security solutions that are tailored to the unique challenges and requirements of each client. Our team engages in a collaborative dialogue with our clients, delving into the specifics of their security landscape to design and implement solutions that are not only effective but also seamlessly integrated into their existing infrastructure, ensuring a harmonious alignment of security and business operations.
Our company's 16-year tenure in the security domain has been a journey of relentless innovation and strategic acumen. We've cultivated an unrivaled expertise, distilling our extensive experience into actionable insights that drive our solutions. Our approach is grounded in a profound understanding of the security landscape, an intimate knowledge of the dynamic threats that shape our world, and a steadfast commitment to innovation. We've navigated the complexities of countless real-world security scenarios, honing our strategies to a razor's edge, ensuring that our clients are equipped with solutions that are not only tried and tested but also poised to tackle the most sophisticated challenges.
Our commitment to quality is the bedrock upon which our product development is built. Each of our products is subjected to a rigorous gauntlet of quality control measures, ensuring that they not only meet but often surpass industry benchmarks. Our products are the embodiment of our dedication to excellence, their durability, reliability, and performance a testament to the meticulous attention to detail that goes into every aspect of their design and manufacture, providing our clients with the assurance that they are investing in the pinnacle of security technology.